So how does censorship feel, Jack? (Issue 20, 2022)
Bitcoin stream suspended, Android apps snoop on millions for US spies, FBI patches firewalls via backdoors, Amazon Alexa pwns itself
We’re delivering you the hottest internet news that affects all of us. Scroll down to read our full reporting below and if you love what we’re doing, please consider contributing $5 per month so that we can continue providing you with this vital, unique reporting.
Talk Liberation is committed to providing equal access for individuals with disabilities. To view an accessible version of this article, click here.
In this edition:
YouTube censors Bitcoin video tweeted by Twitter founder Jack Dorsey
Dozens of Android apps snooping on millions for US spy contractors
Auto maker Subaru adds questionable navigation app to its line
FBI patches firewalls via backdoors while under court order
DuckDuckGo launches new browser while claims of censorship linger
Malware app re-emerges in Google Play to steal passwords, data and messages
Amazon Alexa can pwn itself to buy products and control your home
Clearview AI used to identify the living and the dead in Ukraine
LAPSUS$ and SolarWinds hacks relied upon simple bypass of 2FA
YouTube censors Bitcoin video tweeted by Twitter founder Jack Dorsey
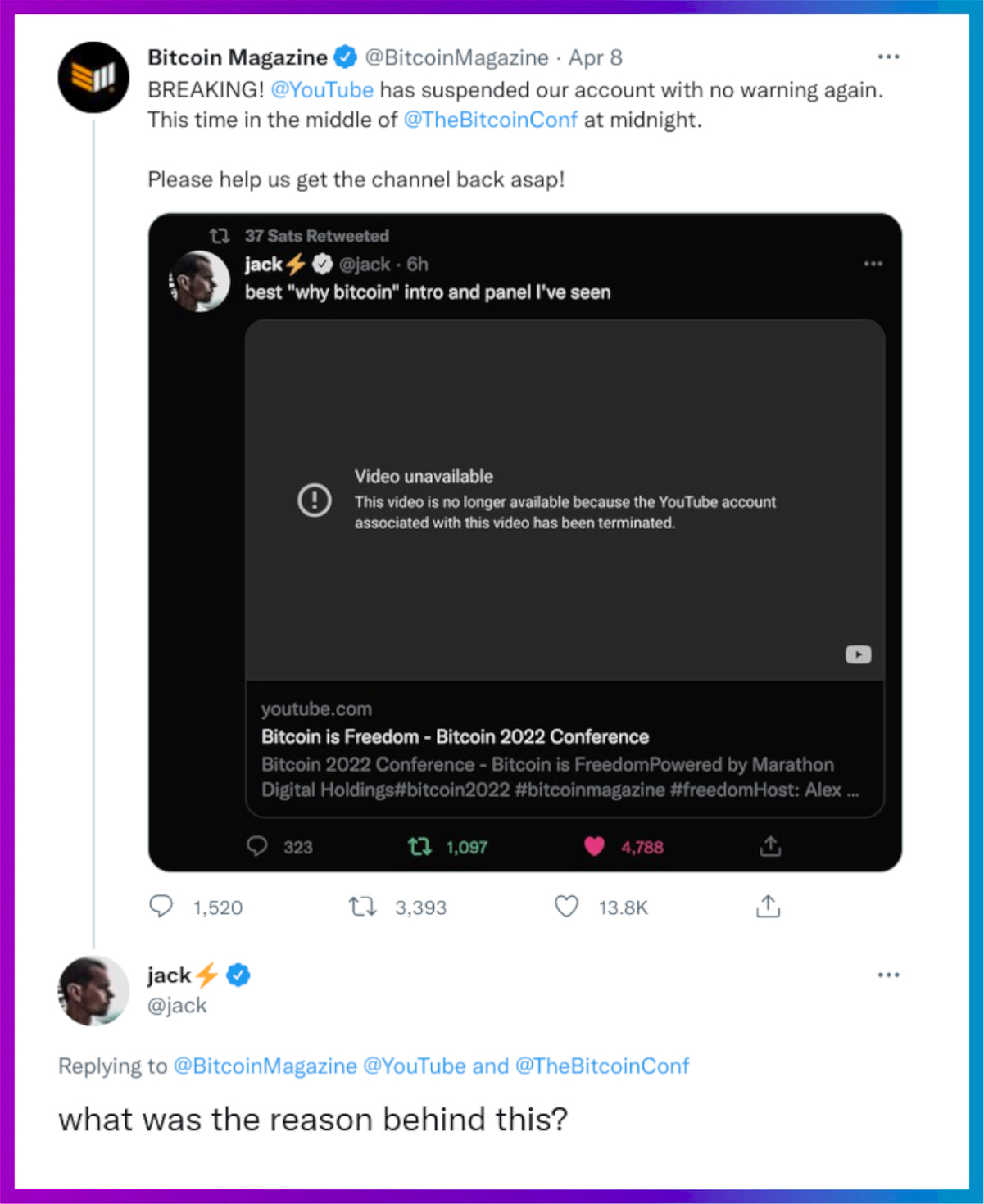
Censorship on Big Tech platforms has reached new heights, with even Jack Dorsey, the founder of Twitter, tangentially affected. Last week, Dorsey shared the human rights panel at the Bitcoin 2022 Conference to his timeline on Twitter. He did so by pasting in the YouTube link to the video stream, calling it the "best 'why bitcoin' intro and panel I've seen."
Unfortunately for Dorsey, his followers, the conference organizers, and the rest of the audience, YouTube suspended the Bitcoin Magazine account shortly afterward — leaving Dorsey to ponder, "what was the reason behind this?"
This high-profile display of social media censorship resulted in a flurry of user comments. One Twitter user summarized the issue with a proverb:
"There’s an old Chinese proverb that goes 'when there’s not enough hot water for everyone to shower, someone is going to be dirty'. [This] seems to be a huge problem with social media these days. A few bad eggs terminating accounts they don’t like for [no] legitimate reason."
YouTube support lifted the suspension later that day, saying the account streaming the Bitcoin 2022 Conference was “incorrectly terminated” and apologizing to Bitcoin Magazine on Twitter. No clarification was made publicly about Google or YouTube policy and no justification for the account termination was disclosed.
Dozens of Android apps snooping on millions for US spy contractors
Spy code has been discovered in dozens of Android apps that were downloaded at least 60 million times from Google Play. These apps have been removed by Google after the discovery by security firm AppCensus, who documented the malicious software development kit (SDK) in detail. The code, dubbed “Coulus Coelib,” is one of the most malicious SDKs ever discovered and collects phone numbers, email addresses, GPS data, and sensitive identifiers such as cell radio information.
The spyware SDK was developed by Panamanian company Measurement Systems. That company is linked by filings to Virginia-based military contractors, companies working for US spy agencies in the Washington D.C. beltway.
The code was found inside Muslim prayer apps, as well as a QR-code scanning app, in addition to other popular consumer apps. Many of these apps had previously included the location-spying X-Mode, an SDK banned by Google in late 2020, SignalFrame, an SDK also associated with US military contractors, and Huq, another SDK penalized by Google.
A 2021 report grouped a cluster of these apps together in Investigation Xoth, a comparative study of a group of SDKs related to X-Mode. X-Mode code included location-nabbing spyware that persisted past its nominal ban by Google.
Now that Coelib spyware has been found inserted into many of the same apps targeting similar audiences, such as practicing Muslims, researchers have raised questions about a closer relationship between all of these SDKs and the companies behind them. Sean O’Brien, Panquake.com CSO and founder of Yale Privacy Lab, bristled at the latest revelations, saying:
“Evidence has piled up over the years that the cluster of apps around X-Mode, Huq, and now Measurement Systems is linked to a US spy operation. Journalistic and technical investigations support this conclusion, and the discovery by AppCensus of Coelib is the latest, most startling, and most direct evidence of this connection to Five Eyes agencies and US Cyber Command. Why does Google allow developers to remove one banned SDK from their apps, and then publish the same apps again in Google Play with new and even more invasive spyware?”
At least one of the apps formerly containing the Coulus Coelib SDK has been published again in Google Play.
Auto maker Subaru adds questionable navigation app to its line
Subaru has plans to upgrade the "infotainment" systems in its vehicles, deploying navigation software provided by What3Words. The car manufacturer joins Ford, Mitsubishi, Mercedez-Benz, Jaguar Land Rover, Lamborghini, and Lotus in shipping this software, as well as China's WM Motors and India's Tata Motors.
What3Words utilizes a non-traditional mapping system that doesn't rely upon latitude and longitude coordinates, instead dividing the map into a grid of 3x3 meter squares. Each of those squares is assigned an identifier comprising of three random words. Supporters of open standards criticize this grid system for being patented and proprietary, in contrast to the standard coordinate system.
What3Words has a history of aggressive legal threats toward security researchers and has attempted to suppress open-source alternatives to its products via takedown notices. Scans from the privacy non-profit Exodus Privacy reveal 11 known trackers from companies such as Facebook, Google, Branch, and Mixpanel in the What3Words app, raising broad privacy concerns.
Despite widespread criticism, emergency and rescue services have embraced the What3Words system in the UK and Australia. This usage has been deemed “not suitable for safety critical applications” by security researcher Andrew Tierney, who pointed out design flaws that result in frequent confusion of grid locations. Reports from the UK seem to support such claims, where rescuers received 45 incorrect locations from users of the What3Words app in a 12-month period.
More than 1,000 organizations license the What3Words application programming interface (API) and software development kit (SDK), including AirBnB, Domino’s Pizza, and the United Nations.
FBI patches firewalls via backdoors while under court order
Network devices infected with a strain of malware were remotely accessed and patched by the FBI, US federal authorities revealed this week. The bulk of the infected machines were firewall appliances sold by WatchGuard, with a smaller amount manufactured by Asus. These two companies issued concurrent security advisories, with WatchGuard stating that it worked "closely with the FBI, CISA, DOJ and UK NCSC" to remediate "Cyclops Blink, a sophisticated state-sponsored botnet."
The international investigation into Cyclops Blink began in November 2021, and the number of machines in the Cyclops Blink botnet fell by 39 percent in February 2022 after the issue became widely known. The FBI decided to take action, receiving court-ordered access to eliminate the rest of the network in March:
“The Justice Department today announced a court-authorized operation, conducted in March 2022, to disrupt a two-tiered global botnet of thousands of infected network hardware devices under the control of a threat actor known to security researchers as Sandworm, which the U.S. government has previously attributed to the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (the GRU). The operation copied and removed malware from vulnerable internet-connected firewall devices that Sandworm used for command and control (C2) of the underlying botnet.”
As with the VPNfilter operation in 2018, the FBI took a high-profile role in removing Cyclops Blink. In this 2022 operation, however, the FBI worked under the cover of a federal warrant. The agency remotely accessed WatchGuard devices, gathered information about other infected devices, scrubbed Cyclops Blink code, and closed ports vulnerable to Sandworm command-and-control.
This is not the first time the FBI has patched machines after utilizing a backdoor to access them remotely. In 2021, the agency remoted into “hundreds” of Microsoft Exchange servers on corporate networks after a court authorized them to remove malware.
Security industry experts have expressed concerns over such operations, pointing out the possible harm to networks and users, and privacy advocates have been alarmed at the potential for abuse and unauthorized access to personal data. In his commentary on the 2021 FBI operation, Dr. David Brumley, CEO and co-founder of ForAllSecure, warned:
"The effort by the FBI… amounts to the FBI gaining access to private servers. Just that should be a full stop that the action is not ok. While I understand the good intention — the FBI wants to remove the backdoor — this sets a dangerous precedent where law enforcement is given broad permission to access private servers.”
Security issues with WatchGuard devices were again in the spotlight this month, with news that the company quietly patched a vulnerability in its firewalls in May 2021 without disclosing the vulnerability to its customers.
DuckDuckGo launches new browser while claims of censorship linger
DuckDuckGo, a US-based company that touts the privacy of its search engine, announced this week that it would be launching a new web browser. DuckDuckGo is now available as an invite-only beta for Mac users.
This browser includes features that will manage cookie consent popups, block trackers, and favor encrypted HTTPS connections when available. It utilizes Apple's WebKit rendering engine, shipped natively with MacOS. DuckDuckGo says a version of its browser will soon be released for Windows as well.
This launch follows a month of controversy for the search engine company. In March, CEO Gabriel Weinberg tweeted that DuckDuckGo would roll out search engine updates to "down-rank sites associated with Russian disinformation." DuckDuckGo also cut ties with its longstanding partner Yandex, a Russia-based search engine, shortly before Weinberg’s announcement.
The changes were met with widespread criticism on Twitter and across with web, with the hashtag #DuckDuckGone trending.
Users expressed their reasons for using DuckDuckGo over Google in the past, explaining that they made the choice to switch not just for DuckDuckGo’s privacy features, but also to avoid the censorship of Big Tech search engines.
Since 2011, DuckDuckGo has vocally condemned the "filter bubble" of competitor Google, releasing a study in 2019 that surveyed Google search results for terms like “gun control,” “immigration” and “vaccination.” The study highlighted Google’s filtering of searches on these hot-button issues.
Though there are recent reports that DuckDuckGo has removed all independent media from its search engine, these claims have been denied by the company and independent news sources still appear in results as of the time of publication.
Malware app re-emerges in Google Play to steal passwords, data and messages
Security researchers reported the re-emergence of malware in Google Play that stole user passwords, SMS messages, and other sensitive data. The malware-infected app was downloaded more than 10,000 times before it was removed.
This remote access trojan, dubbed TeaBot or Anatsa, was initially discovered in May 2021. TeaBot was first designed to steal data from a specific list of apps and targeted approximately 60 banks around the globe. Back then, it utilized streaming to abuse Android’s accessibility services and allow cyber criminals to view and record screen activity, as well as remotely command the smartphone.
This week, researchers at Cleafy reported the existence of TeaBot in the “QR Code & Barcode Scanner” app. The malicious app tricked users into installing a software update that deployed TeaBot on their Android device.
The malware was reported by Cleafy to Google, who removed it from Google Play. Google has come under fire for its lack of oversight and sluggishness in removing malicious apps, even allowing banned spyware to persist in its marketplace after Google claimed it was eliminated.
Amazon Alexa can pwn itself to buy products and control your home
In an exploit demonstration dubbed "AvA" or "Alexa vs. Alexa," Amazon smart speakers can be forced to unlock doors, purchase items online, make calls, and control smart home appliances. The attack utilizes the Amazon speaker itself to speak to its own microphone, triggering the device's voice command functionality via a wake word (such as "alexa" or "echo").
Essentially, you can ask Alexa to tell Alexa to do something nefarious. Software-provided safeguards are trivial to bypass using the word "yes" shortly after issuing a command. Controls like auto-reduction of speaker volume while the voice assistant listens for commands can also be circumvented — what the researchers call "FVV" for "full voice vulnerability".
The attack can take place in just a few seconds, starting with a person close to a vulnerable Amazon speaker. The attacker says a voice command telling the speaker to pair with the attacker's Bluetooth BLE device and, while the attacker is still in radio range, they can initiate commands.
This is not the first attack to bypass controls over voice activation systems and send unauthorized commands from a distance. In 2019, it was demonstrated that attackers could trigger commands to smart speakers using Alexa, Siri, or Google Home software via short or long-range laser beams shining on the device. This optical-acoustic effect is poorly understood, exploiting the material properties of Microelectromechanical systems (MEMS).
Clearview AI used to identify the living and the dead in Ukraine
As covered in previous editions of Talk Liberation, the controversial Clearview AI facial recognition company has been found in violation of federal laws in Australia, banned in the EU, and debated in the US Congress over its use by government agencies. It has also been fined by the UK government for scraping billions of photos from sites such as Facebook, Instagram, and LinkedIn.
In March, the company’s chief executive Hoan Ton-That claimed it was providing assistance to the Ukraine Defense Ministry. Now, the BBC reports that Clearview AI is being used by Ukrainian authorities to identify the dead, people who are stopped at checkpoints, and suspects in detention.
The biometric app was offered by Ton-That to the Ukrainian government for free, and the company claims to have obtained more than two billion images from the Russian social media platform VKontakte. Clearview AI also boasts that the company’s technology could better identify a deceased person than fingerprint biometrics.
In an exclusive statement to Talk Liberation, Jack Poulson, Executive Director of Tech Inquiry, warned not to take any statements from Clearview AI at face value:
“While Clearview AI has less than half of the (publicly disclosed) U.S. federal moneyflow for facial recognition as RealNetworks and TrustStamp, many of its deployments are on a trial basis. Further, a leaked December 2021 pitch deck revealed CEO Hoan Ton-That's clear deception over the company's planned expansion into the gig economy, finance, and entertainment. As a result, all unconfirmed assertions from the company should be treated with skepticism.”
The latest reports confirm the usage of Clearview AI on and off of the battlefield in Ukraine. The accuracy of this facial recognition is still questioned by experts. In the BBC report, facial recognition expert Conor Healy stated, "It's important for the Ukrainian forces to recognize that this is not a 100% accurate way of determining whether somebody is your friend or your foe."
Privacy advocates have issued strong warnings about the situation. In a statement to Forbes, Albert Fox Cahn, Executive Director of the Surveillance Technology Oversight Project, called it "a human rights catastrophe in the making" and cautioned, “When facial recognition makes mistakes in peacetime, people are wrongly arrested. When facial recognition makes mistakes in a war zone, innocent people get shot.”
LAPSUS$ and SolarWinds hacks relied upon simple bypass of 2FA
Multi-factor Authentication (MFA), popularly called "2FA" for Two-factor Authentication, can take many forms. Some methods are very strong and resistant to exploitation, while other methods such as SMS and phone authentication are prone to abuse by cyber criminals. Push prompts sent to smartphones make users especially vulnerable, and it is this method that has been exploited in high-profile attacks by LAPSUS$ and in the SolarWinds breaches
Though this method of utilizing MFA to bypass security controls requires persistence, the approach is simple. A post to the LAPSUS$ Telegram channel explained one version of the process:
"No limit is placed on the amount of calls that can be made... Call the employee 100 times at 1 am while he is trying to sleep, and he will more than likely accept it. Once the employee accepts the initial call, you can access the MFA enrollment portal and enroll another device."
The LAPSUS$ group has breached Microsoft, Nvidia, and Okta this year and is reportedly comprised of teenage hackers. “While it may be tempting to dismiss LAPSUS$ as an immature and fame-seeking group, their tactics should make anyone in charge of corporate security sit up and take notice,” said security expert Brian Krebs, in his post about the group.
Similar methods have been dubbed “MFA prompt bombing” in the past, as described in detail by Twitter user _MG_, a well-known penetration tester, and security researcher Greg Linares.
Stronger forms of MFA that are tied to a physical machine in use by the end-user, such as FIDO2 and physical key tokens, are not susceptible to these techniques. However, they are not immune to attacks that utilize social engineering.
That concludes Your Worldwide INTERNET REPORT for this week!
Remember to SUBSCRIBE and spread the word about this amazing news service.
Talk Liberation - Your Worldwide INTERNET REPORT was brought to you by Panquake.com. We Don’t Hope, We Build!
© Talk Liberation Limited. The original content of this article is licensed under a Creative Commons Attribution-ShareAlike 4.0 International license. Please attribute copies of this work to “Talk Liberation” or talkliberation.com. Some of the work(s) that this program incorporates may be separately licensed. For further information or additional permissions, contact licensing@talkliberation.com







Who is the author of this article? Thank you.