What are you really getting with GETTR?
As people seek an alternative to Big Tech abuses, GETTR has gained millions of users. This exclusive investigation by Talk Liberation reveals the troubling tech behind GETTR that puts users at risk.
Is GETTR a social media revolution or does it emulate the same Big Tech platforms its users are eager to escape?
GETTR bills itself as a place to "break away from Big Tech," emphasizing that it not only delivers "unfiltered discourse" but "values your privacy." In this exclusive report, Talk Liberation Investigates digs into these claims, analyzing the GETTR website and smartphone apps.
“Given all that we’ve learned about GETTR, the bottom line isn’t about what you’re getting from them. It is about what they’re getting from you.”
Key Findings
Numerous trackers from Facebook, Google, and other third parties are embedded in GETTR web and smartphone apps.
App permissions facilitate the surveillance of a wide variety of information about GETTR users, including fine-grained behavior and location data. This data is then used to profile users and shared with third parties.
“Getome,” a previous version of the GETTR app that targeted Chinese-language audiences, is still published in Google Play and effectively provides a backdoor to GETTR. Users can log in and interact on the GETTR network via the Getome app, bypassing updates on the newer application.
Content on GETTR such as news is loaded directly from external sources, opening connections between GETTR users to dozens of domains. This introduces serious privacy and security risks. Some of this content is delivered via unencrypted HTTP, further jeopardizing users.
GETTR’s privacy policies fail to disclose the full extent of GETTR data collection and sharing with third parties.
GETTR infrastructure is hosted by cloud vendors such as Amazon AWS and company email accounts are hosted by Google.
Utilizing the API of GETTR to gather large amounts of data is trivial. The situation has improved since approx. 90,000 emails were breached in July 2021, but a trove of information is still available via basic technical methods.
“After a multi-faceted, technical analysis of GETTR, it is evident that the platform is not at all ‘safe from the Silicon Valley Mafia’s tyrannical overreach,’ as they claim.”
Our Investigation
To view the source data for this investigation, see the repository at https://github.com/TalkLiberation/investigates-gettr
Contact media@talkliberation.com for media inquiries and more information.
Like this report? Subscribe to Talk Liberation to support more research.
Our analysis was conducted on web and smartphone apps by Sean O’Brien, CSO of Panquake.com and founder of Privacy Lab at Yale Law School, where he also teaches Cybersecurity. This study utilized Free and Open-Source Software (FOSS) tools and publicly-available sources. Please be aware that this is technical research and not legal analysis, therefore none of the materials within should be construed as legal analysis or advice.
While working on this research, Talk Liberation Investigates identified a vulnerability whose severity was responsibly disclosed to GETTR. GETTR’s engineering team has acknowledged the report and is working on the issue. These materials will be updated appropriately, after the fix has been verified.
Note: Please see the update at the bottom of this article for our response to GETTR’s comments on this research.
For smartphone app analysis, we focused on Android due to the uncertain legal status of certain types of analysis on Apple iOS. That said, Apple customers should expect the concerns we outline in this report to broadly apply to iOS versions of GETTR. Studies consistently prove that iPhone users suffer from pervasive tracking. GETTR discloses some of its data-collection activity in the iOS App Store.
Before we dig into the technical problems with GETTR, some background on the social network’s surge in popularity and its murky origin is required.
Out of the frying pan
A growing number of Internet users are flocking away from Big Tech social media platforms such as Facebook, Twitter, Instagram (owned by Facebook), and YouTube (owned by Google). Big Tech was again under scrutiny in 2021, with networks that contain billions of users facing a constant stream of negative press. Facebook led the rogue's gallery, rebranding its parent company to "Meta" after a series of disclosures about internal practices and the harms caused by both the Facebook network and Instagram.
Alongside Facebook, Twitter and YouTube leaned into the AI-powered, algorithmic moderation they ramped up at the start of the Covid-19 pandemic. Big Tech social media has escalated the removal of conservative political figures and allegedly right-wing content, while also censoring artists and journalists who identify with left-wing politics. In a world where following Twitter's own policies around renaming accounts can result in a permanent ban, it's not difficult to see the appeal of alternatives.
At the start of 2022, GETTR swelled to nearly 4 million users, reflecting a rising discontent with Big Tech and its policies of censorship and surveillance. GETTR has harnessed this energy alongside a strong push by US political figures and celebrity conservatives. This includes an endorsement from Representative Marjorie Taylor Greene, who was banned from Twitter, as well as former secretary of state Mike Pompeo and media personalities such as Sean Hannity. Former President Trump, however, is backing his own venture called Truth Social.
“Content on GETTR such as news is loaded directly from external sources, opening connections between GETTR users to dozens of domains. This introduces serious privacy and security risks. Some of this content is delivered via unencrypted HTTP, further jeopardizing users.”
In an appearance by Dr. Robert Malone on the Joe Rogan Experience podcast, Dr. Malone mentioned GETTR as an alternative to Big Tech censorship. Joe Rogan joined GETTR soon after the interview, “Just in case shit over at Twitter gets even dumber.”
This brought massive media attention and a throng of new users to the network.
GETTR 2.0
The current version of GETTR officially launched on July 4, 2021 against the backdrop of Big Tech malfeasance, promising to differentiate from these megacorps by "challenging social media monopolies and creating a true marketplace of ideas."
GETTR is helmed by CEO Jason Miller, a former senior advisor to the Trump administration. Chinese billionaire Guo Wengui bankrolled the development of GETTR and this backing has been confirmed by Miller, though he denies Guo has any official authority in the current venture.
Reports about Guo have emphasized his ties with Steve Bannon, who has been involved in social media since his time as vice president and board member of Cambridge Analytica. The firm infamously harvested personal data on at least 50 million Facebook users in order to profile individual US voters and target them with personalized political ads in the lead-up to the 2016 US presidential election.
“Like Twitter and Facebook, sponsored news stories appear next to the timeline. It is evident that this content is curated and not derived organically from network activity or trends.”
As has been previously reported in Politico and other outlets, the first version of GETTR was a Chinese-language platform called “Getome” and a part of Guo and Bannon’s GNEWS and GTV properties. “Bannon’s War Room” is featured prominently on GNEWS, where GETTR is still promoted alongside GTV assets.
In the week prior to Miller's Fourth-of-July launch of GETTR in the US, a Mandarin message for viewers of GNEWS reminded platform users to "follow instructions" because the network is "not ours" and explained that "GETTR is cleaning up all the data and accounts. Afterwards, everybody has to re-register their accounts."
This quiet wipe and repackaging of GETTR lies in stark contrast to the furore in the US surrounding other apps tied to China. In 2020, then-President Trump attempted to ban TikTok and US politicians labeled the app a "national security threat."
Getome gets you into GETTR
Technical analysis by Talk Liberation Investigates has confirmed that the Getome apps are earlier versions of GETTR. Additionally, our testing has discovered:
Getome is still published in Google Play. This outdated app can log into the GETTR network with a GETTR account, follow other users, and introduce content into the network.
The first release of the Getome app for Android lists “V MAGA” as the developer with a “prayfor2022” email address and was uploaded May 9, 2021.
The last release of the Getome app for Android currently lists “GETTR USA, Inc” as the developer and has not been updated since June 9, 2021 — days before it was effectively cloned and rebranded to GETTR.
This last version of Getome might still be made available to provide users a smoother transition to the rebranded GETTR. However, this is bad security practice. In the event of GETTR updating their latest releases to patch for security vulnerabilities, these fixes will never be pushed to the old Getome versions. This puts the segment of users still running Getome apps at risk.
In testing, Talk Liberation Investigates found it was possible to not only download and install Getome on the most recent Android OS, but that the app would allow users to log into the GETTR network, search for and follow other users, and post.
Updates should either be “backported” to older Getome versions or that software should be abandoned and blocked from connecting to the GETTR network. As new features, rules, or restrictions are added to GETTR — say, to restrict bots from auto-following accounts — old Getome apps become a liability that might be exploited to ignore these changes. Moderation changes have already been introduced to newer versions of GETTR that are not in Getome.
Same as the old boss
During testing by Talk Liberation Investigates, it became clear that GETTR is an example of a Web 2.0 app that closely resembles Twitter in its user interface (UI) and user experience (UX) as well as architecture.
Like Twitter and Facebook, sponsored news stories appear next to the timeline. It is evident that this content is curated and not derived organically from network activity or trends. Users are recommended to follow specific users, primarily popular celebrity accounts. Even if a user has no followers, their timeline fills in with content from accounts such as CEO @JasonMillerInDC.
The user experience is reminiscent of Big Tech platforms. In recent years, follower suggestions and curated content have been criticized, especially the kind of algorithmic manipulation seen on Facebook and Twitter. This is often powered by artificial intelligence (AI) or machine learning (ML) that is trained with troves of data about user behavior.
News and video content under the header “GETTR News” does not appear to be ranked or reordered based upon such algorithms, likely being picked manually by GETTR admins instead. However, follower suggestions and timeline content do appear to use such algorithms.
“The GETTR app asks for a total of 34 permissions, including many that are deemed sensitive or problematic. Taken together, these permissions give GETTR substantial control over a device and provide ample opportunity for surveillance.”
GETTR users are also reporting bot and spam activity, including an influx of followers of dormant or brand new accounts. This behavior was witnessed by Talk Liberation Investigates as well, where a dummy user created for testing was immediately followed by a spam account.
In GETTR, there is no clear separation between content and data that originates with Twitter. Celebrity accounts such as @JoeRogan are provided with heavily-inflated statistics in the millions — in Rogan’s case, more than double the total number of users on GETTR. These numbers are based upon Twitter follower counts. Additionally, thousands of tweets can be imported to a GETTR account with no indication that these are historical archives.
Other UI/UX elements in GETTR reflect Big Tech and Web 2.0 sensibilities. For example, signing up for GETTR requires an email address. An email is sent to that address with a verification code. Such email address disclosure is Web 2.0 standard practice, and GETTR does not block disposable email. However, there are potential privacy issues with GETTR’s process for collecting your email address.
First, the verification email is sent via third-party vendor Postmark and no information concerning potential storage and mining by Postmark is disclosed. Second, the message travels through a Google email domain reserved for GETTR customer support.
If emails for new users are being cached with Google and other third parties, privacy is evidently not a priority — let alone avoidance of Big Tech’s gaze.
“GETTR users are also reporting bot and spam activity, including an influx of followers of dormant or brand new accounts. This behavior was witnessed by Talk Liberation Investigates as well, where a dummy user created for testing was immediately followed by a spam account.”
Connected to dozens of domains
GETTR emphasizes that the platform “values your privacy and will never sell or share your personal information, so you can rest assured it's in good hands.” A cursory analysis of the GETTR web app disproves this statement, and more detailed analysis reveals troublesome trends that mimic the Big Tech surveillance machine and contribute to its data collection.
Talk Liberation Investigates found that:
The gettr.com web app loads tracking cookies and pixels from Google and Facebook that create unique identifiers for individual users. GETTR users are surveilled by Big Tech across websites and devices and this tracking creates persistent, targeted ads and “filter bubbles.”
Third-party trackers such as AppsFlyer and Countly are utilized by GETTR for web browser fingerprinting and to collect behavioral data about users.
A large amount of JavaScript code is delivered via cloud CDNs such as Amazon AWS and Cloudflare in addition to embedded content that is directly loaded from around the web. As users browse GETTR, they are connected to literally dozens of domains simultaneously.
GETTR utilizes a variety of third-party services for user communication and support. Transparency about GETTR’s relationships with these parties is lacking. They include ZenDesk, Postmark, Mailgun, and SolarWinds Pingdom.
For a platform that advertises itself as a break from Big Tech, the inclusion of a variety of Google and Facebook advertising trackers is disingenuous. These trackers are responsible for the creepy behavior associated with cross-device tracking and ad "personalization." Cross-device tracking creates a footprint that persists across a person's digital life, a point the US Federal Trade Commission (FTC) emphasizes:
Cross-device tracking occurs when platforms, publishers, and ad tech companies try to connect a consumer’s activity across her smartphones, tablets, desktop computers, and other connected devices. The goal of cross-device tracking is to enable companies to link a consumer’s behavior across her devices.
Thus, the targeting that follows a person’s day-to-day experiences — when they watch a smart TV, browse their smartphone, walk past a storefront, or even use the bathroom — can often be traced back to interactions on social networks like GETTR.
For a platform that advertises itself as a break from Big Tech, the inclusion of a variety of Google and Facebook advertising trackers is disingenuous. These trackers are responsible for the creepy behavior associated with cross-device tracking and ad "personalization."
GETTR loads two Big Tech cookies that promote persistent, cross-device surveillance:
GETTR’s usage of additional trackers by data brokers compounds the problem. This includes two cookies by AppsFlyer:
Talk Liberation Investigates discovered particularly aggressive surveillance by AppsFlyer, which conducts browser fingerprinting via the web browser’s “canvas” element and font configuration. The combination of these settings is correlated with unique identifiers and utilized to record user behavior, such as clicks.
Groups such as the Electronic Frontier Foundation (EFF) have been warning about browser fingerprinting for many years, and these techniques pose a particular risk to users who attempt to remain anonymous via technology such as Tor. Other notable recommendations from the EFF and digital rights groups are absent from GETTR, including page headers that disable Google’s emerging cookie-less tracking technology, Federated Learning of Cohorts (FLoC).
Countly is yet another tracker utilized by GETTR throughout the network, “explor[ing] user behavior on an individual level of detail.” In addition, both technical and UI/UX testing reveals a variety of third parties being utilized for customer support services, website monitoring, and website statistics. This includes ZenDesk, Postmark, Mailgun, Google Analytics, and SolarWinds Pingdom.
The fine print
As previously noted, Talk Liberation Investigates has analyzed GETTR from a technical standpoint and does not provide legal analysis or advice. However, it is important for readers to be made aware of GETTR policies in general terms, where it relates to the public interest.
“GETTR's practices do not appear to abide by GDPR’s strong rules in regard to informed, opt-in consent.”
The growing backlash against technology like the tracking cookies, pixels, and JavaScript surveillance in GETTR is embodied in legislation such as the EU/EAA General Data Protection Regulation (GDPR). GDPR is the primary reason users now see cookie disclosures and consent popup messages across many of the websites they visit. There is a distinct lack of these disclosure and opt-in consent mechanisms on GETTR, considering the wide array of clandestine tracking mechanisms on the platform.
Our technical analysis has identified wholly US-based infrastructure for GETTR, primarily with cloud vendors such as Amazon AWS, Cloudflare, Rackspace, Fastly, and Google email. Domains associated with GETTR are registered with Epik, and even past domains that remain from the previous iterations of the network, such as getome.com and getter-qa1-tk, resolve to US-based servers.
This architecture fully embraces Web 2.0 cloud topology, utilizing strong centralization and ignoring the trend toward decentralization that has emerged in “web3” and federated social networks.
There are a number of reasons why a US-based tech company might be bound to regulations in Europe. For example, whether the GDPR applies to a company’s data practices is dependent on where a user ("data subject") is when their data is processed, and not the citizenship or nationality of that user.
GETTR's privacy policy has a jurisdiction-specific section concerning EEA and UK privacy, assuring users in these jurisdictions that they process personal data for a variety of legal reasons including "where you have given consent to our specific use." It continues by outlining rights described in GDPR, without naming regulations.
This is unlikely to cover the extent of data collection and sharing discovered by Talk Liberation Investigates. Specifically, GETTR's practices do not appear to abide by GDPR’s strong rules in regard to informed, opt-in consent.
Though the GETTR privacy policy and terms of use disclose the usage of Google ReCAPTCHA and Google Analytics, pointing users to Google’s policies, no other third parties are mentioned. Opt-out mechanisms for targeted advertising are described by GETTR, though the policy admits that such mechanisms are likely temporary and not comprehensive. Web browser “Do Not Track” signals are ignored by GETTR.
All GETTR users deserve strong privacy protection, wherever they live and travel. Though the US privacy landscape is current a hodgepodge of legislation, US-based users are increasingly demanding privacy measures that emphasize transparency and consent. As GETTR’s userbase grows, lack of disclosure and autonomy in regard to user privacy will increase liability and risk for both the GETTR platform operators and end-users.
GETTR follows your location
Smartphones are a privacy minefield. Apps on Android and iOS contain hidden trackers, usually bundled in an app as a Software Development Kit (SDK). An SDK is a package of code that provides functionality in an app, and may include useful features that the developers would otherwise have to write from scratch. However, these SDKs often include advertising-based surveillance, location tracking, and other anti-features that create privacy harms for end-users.
Talk Liberation Investigates identified 9 tracker SDKs in GETTR smartphone apps:
AppsFlyer
Countly
Facebook Analytics
Facebook Login
Facebook Share
GIPHY Analytics
Google AdMob
Google Crashlytics
Google Firebase Analytics
These SDKs were identified using tools provided by Exodus Privacy and verified via static analysis. Of these, AppsFlyer appears to be the most aggressive, assigning a unique and persistent identifier that can be used for cross-device tracking. This strongly mirrors the AppsFlyer implementation in the GETTR web app.
Using tools provided by Defensive Lab Agency, specific information about the types of data accessed by trackers in GETTR has been represented in “call graphs.” In this example, the AppsFlyer tracker accesses smartphone location information:
These call graphs clearly demonstrate that a variety of information can be used to target users and fingerprint smartphones via GETTR. This includes network information such as IP address, cell network provider, operating system version, phone model, and both coarse and fine-grained location information.
Additionally, the GETTR app asks for a total of 34 permissions, including many that are deemed sensitive or problematic. Taken together, these permissions give GETTR substantial control over a device and provide ample opportunity for surveillance.
In the past year, both Apple iOS and Google Android have recognized the importance of app permissions as the front line of smartphone privacy. If an app is expecting you to blindly accept numerous permissions just to use it, it is wise to avoid the app altogether.
Unencrypted traffic
As described earlier, GETTR connects to numerous external domains to load content for the user such as news articles and video streams. Research by Talk Liberation Investigates has revealed security issues with this architectural choice.
GETTR subjects users to weak SSL/TLS implementations from external sources.
At least one SSL/TLS certificate deployed by GETTR utilizes an insecure 3DES cipher.
Security headers, referrer headers, and other defaults required for web apps to adhere to standard security practice are missing.
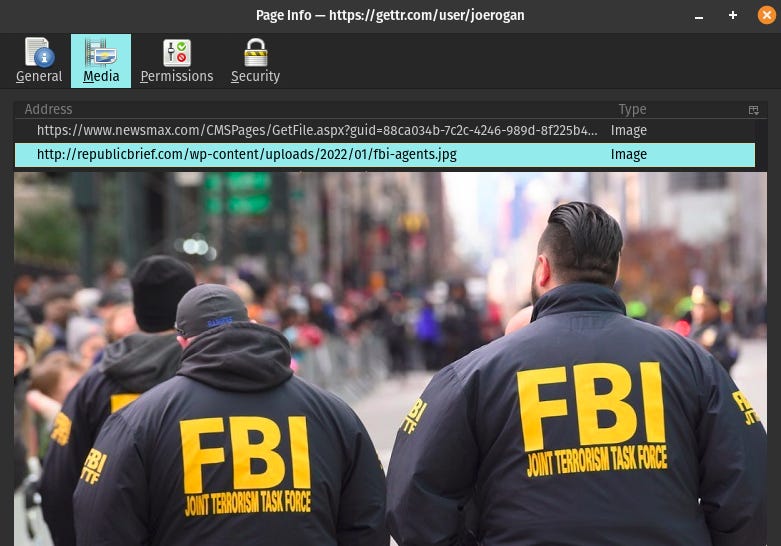
GETTR loads mixed and unencrypted HTTP content in the network, including images.
This introduces the serious potential for malware injection and subjects users to surveillance by the originating source.
Talk Liberation Investigates identified at least one case where content was unambiguously loading via plain, unencrypted means. Perhaps ironically, it concerned a news article about the FBI and a photo of FBI agents:
This is both a major privacy concern and a separate security concern. The privacy concern is that the server the content is loaded from could have logged information about the web browser and operating system. Given common defaults for modern web servers, it almost certainly did — and GETTR users would be none the wiser.
Of course, law enforcement and anyone watching the network (say, on a university campus) could also see this unencrypted HTTP traffic and record information about the user.
The security concern is that malicious content could have been injected, and exploits concerning image files occur regularly. It’s not difficult to imagine malware propagating through GETTR given the current architectural choices.
This “FBI” image was loaded via GETTR’s curated news feed and therefore downloaded by all users who logged in that day. Though such attacks are not limited to unencrypted traffic, targeted attacks against a specific user or group of users could be made more viable by plain HTTP traffic.
“Talk Liberation Investigates identified at least one case where content was unambiguously loading via plain, unencrypted means.”
Beyond risk and mitigation, “hotlinking” content directly from someone else’s web server is bad etiquette and passes bandwidth, cost, and liability onto the source. For this reason, some websites will ban visitors and entire networks from embedding content this way. If GETTR admins continue to hotlink, they will eventually find websites banning them from doing so.
Catching flies with honey
It is no surprise that GETTR, a network launched by former Trump advisors and connected to Steve Bannon, might be the target of intelligence-gathering by political rivals, hackers, and spies utilizing OSINT or SOCMINT methods. Despite this, the current state of social media is so horrific that nearly any alternative is a breath of fresh air to people who are perpetually abused by Big Tech.
The concerns outlined in this report are relevant to the people rushing to join GETTR — including the 1 million who joined in early 2022 — as well as users on other platforms that market to a similar core audience (e.g. Gab, Parler, and the upcoming Truth Social). Instead of attempting to analyze these other networks from a technical standpoint, recent history can instead provide insight, awareness, and warning.
“The GETTR API, together with bot activity inside the network, could be utilized to scrape vast amounts of data on users and map large parts of the social network.”
In the past few years, the privacy breaches and security incidents at Gab, Parler, and Epik are so numerous that it can be difficult to separate them. GETTR is a part of this cluster of platforms, relying upon Epik as a domain registrar and service provider.
Just days after the official launch in July 2021, GETTR faced major hurdles. Besides being flooded with explicit images, the GETTR API was scraped to reveal the usernames, locations, and email addresses of 90,000 users. Despite this privacy breach, the GETTR API is still very much open to scraping without any verification method (such as an API key).
Talk Liberation Investigates utilized freely-available and FOSS tools to reveal a small amount of information on dummy user accounts created specifically for this research. During this testing it became obvious that the GETTR API, together with bot activity inside the network, could be utilized to scrape vast amounts of data on users and map large parts of the social network. Though email address and location is no longer available, the GETTR API can be queried by anyone with basic technical skills to discern:
All posts or comments from a specific user on the platform
All of a user's followers
All users a specific user follows
All comments on a specific post
All profile information about a specific user
All hashtags marked “trending”
All posts marked “trending”
All suggested users
While testing the tool provided by Stanford Internet Observatory, there appeared to be no rate-limiting, queueing, or defensive measures in regard to scraping the GETTR API for lists of users and their relationships.
Readers of Talk Liberation Investigates will be familiar with our ongoing investigation into WLDragnet — the targeting of WikiLeaks supporters, free speech advocates, journalists, and activists. Just as Twitter users can be mapped and targeted for their perceived relationships and influence on conversations, GETTR can be utilized for the same outcomes.
The bottom line
After a multi-faceted, technical analysis of GETTR, it is evident that the platform is not at all “safe from the Silicon Valley Mafia’s tyrannical overreach,” as they claim. It is also clear that GETTR has major privacy, security, and design pitfalls of its own.
People seeking to jump ship from Big Tech platforms that have spied on and commodified them for years should be cautious and understand that alternatives may contain flaws in their design and implementation. Often, this insight is only gained after public scandal triggered by data breaches or other detrimental user experiences.
Talk Liberation Investigates has compiled this report to empower users to take steps to mitigate the privacy and security threats they may not have been otherwise aware that they face. We are committed to informing, educating, and liberating Internet users from those who seek to abuse them for commercial or political gain.
Given all that we’ve learned about GETTR, the bottom line isn’t about what you’re getting from them.
It is about what they’re getting from you.
Disclosure: Sean O’Brien is the Chief Security Officer of the upcoming crowdfunded social media platform Panquake.com, which harnesses ethical design, privacy-respecting architecture and cutting-edge technological advances to break the existing paradigm of user exploitation by conventional social media platforms.
Update: Since publishing this article, our findings have been cited in multiple other publications and have resulted in a lengthy email to Talk Liberation from GETTR’s Global Communications Director. The email contained nine “specific responses” from GETTR’s CEO, former Trump advisor Jason Miller and a request that we make these public. In this Twitter thread (archived version here), Sean O’Brien obliges, publishing a series of screenshots containing Miller’s responses to this reporting.
This post by Talk Liberation Investigates was written by Sean O’Brien and edited by Suzie Dawson.
Talk Liberation Investigates is dedicated to Eynelys Garcia, our exceptionally talented, caring and dedicated Digital Media Team Coordinator who recently passed away in a tragic hit and run accident. Eynelys is survived by her disabled younger sister, and her mother who is fighting cancer. Please join us in supporting Eynelys’s family here.
Talk Liberation Investigates is brought to you by Panquake.com. We Don’t Hope, We Build!
© Talk Liberation Limited. The original content of this article is licensed under a Creative Commons Attribution-ShareAlike 4.0 International license. Please attribute copies of this work to “Talk Liberation” or talkliberation.com. Some of the work(s) that this program incorporates may be separately licensed. For further information or additional permissions, contact licensing@talkliberation.com















This looks like the go-to reference about GETTR and generally for how this kind of work is done!
Well done to all involved.
Excellent work, Sean! Much appreciate this insight into GETTR - I knew they looked pretty fishy (phishy? lol) but they're much worse than I expected. I hope this information spreads quickly.